Developing Secure Component-Based Software

 In many cases one of the core requirements on IT systems is to ensure confidentiality of processed data. This is especially true, if sensitive or personal data is processed. One goal of KASTEL is to provide a method that allows the systematic elicitation of requirements during the design of the system and that makes it possible to keep these requirements consistent over different stages of the development process.
In many cases one of the core requirements on IT systems is to ensure confidentiality of processed data. This is especially true, if sensitive or personal data is processed. One goal of KASTEL is to provide a method that allows the systematic elicitation of requirements during the design of the system and that makes it possible to keep these requirements consistent over different stages of the development process.
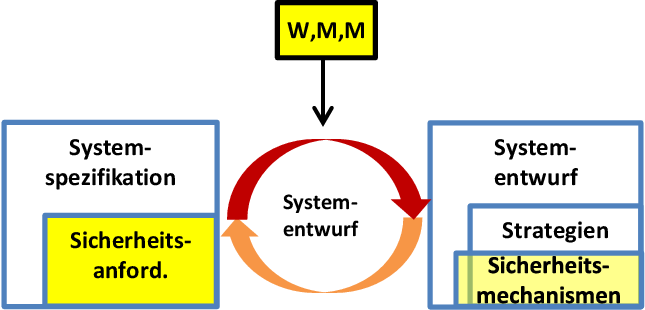
Therefore, KASTEL developed a model-based approach for the specification of security requirements in component-based systems. The specification can be checked for consistency over different stages of refinement of a system and can be used to prove requirements for the implementation of single components. On the architectural level, we employ and extend the Palladio Component Model.
Model-Based Specification of Confidentiality Requirements
In order to ensure with our approach that confidential data is only accessible by authorized persons, it is necessary to specify which data is confidential. This confidentiality specification is necessary, on the one hand, to be able to detect unwanted information flow between components already at design time. On the other hand, it is necessary at the end of development in order to be able to prove that a specific implementation meets the specification. The confidentiality specification in our approach indicate,
- which parameters and return values of software interfaces may be known by which user roles,
- how hardware and runtime environment influence the confidentiality of processed data,
- which adversary types with which capabilities should be considered and which data may be known to these adversaries.
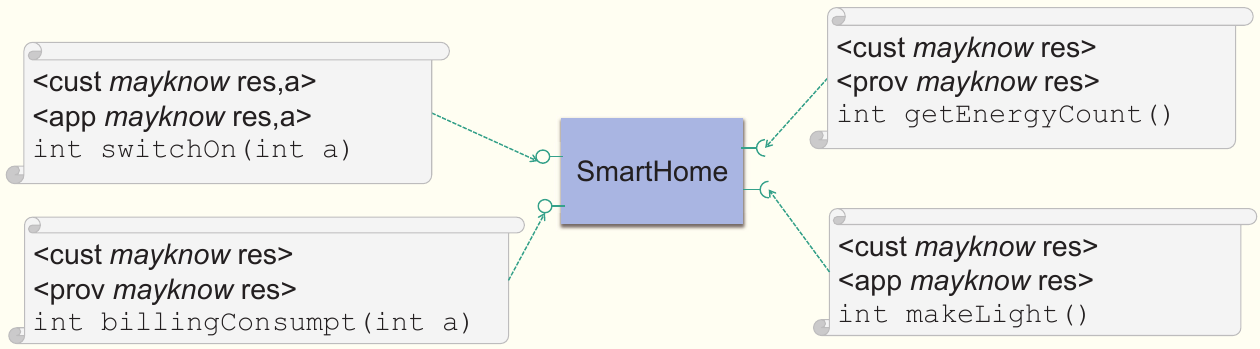
Let us consider a smart-metering system, which is able to reveal the electric power consumption of a household and its individual appliances using digital electricity meters. For such a system a confidentiality specification for our approach could be, for example, as follows: At the interface of the smart meter, it is specified that the energy consumer and the energy provider roles may be able to read the current count of the meter. Only the consumer is, however, allowed to read the consumption of individual appliances and consumption data split to the second. The energy provider may only know the total consumption of the household in aggregated form, for example using blocks of 15 minutes. Both requirements can be expressed with a single-lined annotation in the architectural model and are also understandable for non-security experts. In addition, for the hardware of the system it may be specified, for example, whether influences of other software components that operate on the same hardware have to be anticipated or which user roles may have physical access to the hardware. Finally, it can be expressed, for example, that an adversary with access to the data of the energy provider and physical access to the meter should be considered.
Model-Based Specification of Communication Channels
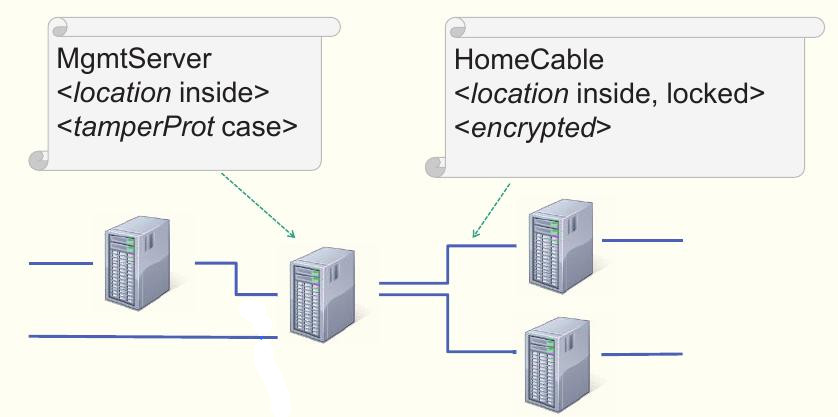 In distributed component-based systems, the security related characteristics of communication between the subsystems became important. For this reason, the characteristics of communication channels must be considered as early as possible in development process. Therefore, we developed an approach to model the communication channels with respect to their security related characteristics. The modeling approach is suitable for tool supported verification of a system design with regard to the accordance of its security properties.
In distributed component-based systems, the security related characteristics of communication between the subsystems became important. For this reason, the characteristics of communication channels must be considered as early as possible in development process. Therefore, we developed an approach to model the communication channels with respect to their security related characteristics. The modeling approach is suitable for tool supported verification of a system design with regard to the accordance of its security properties.
For channel modeling, we considered security requirements for confidentiality, integrity, authentication, and access control. Furthermore, we educed a catalog of generic threats on communication transactions to investigate potential attacks already in the modeling stage of development process. Confidentiality related characteristics of communication channels are locality, tamper-protection, access-control and encryption. Access-control states whether control on access, in order to use the channel for communication, is provided and encryption indicates the support for confidentiality by encryption of the message payload.
Model-Based Information Flow Specification
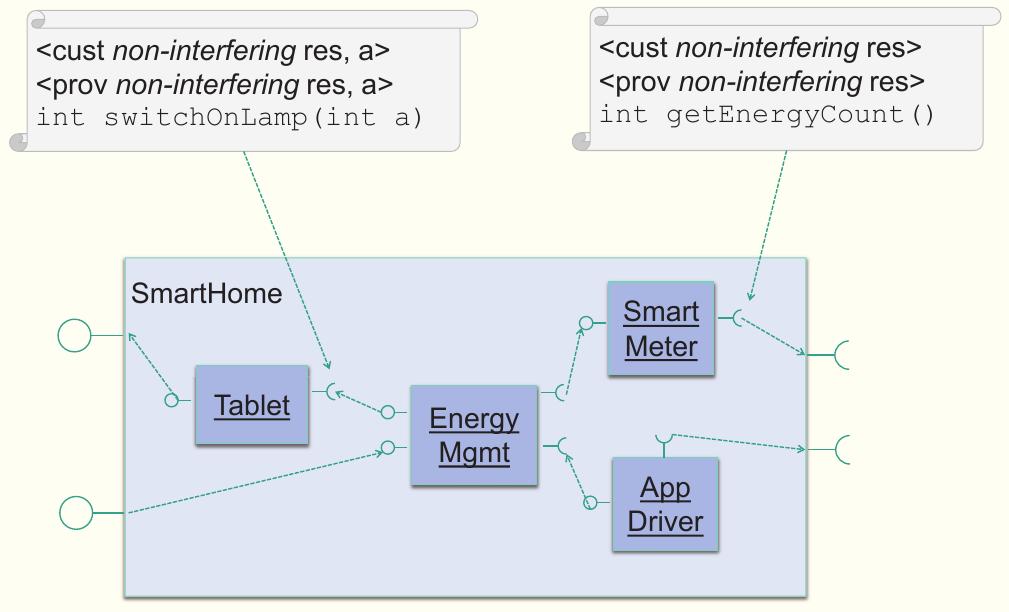 Using the specification methods mentioned above, we are able to formalize the restrictions on the access to data available through the systems interfaces. Additional specification methods, however, are required to state restrictions on the information encoded in this data.
Using the specification methods mentioned above, we are able to formalize the restrictions on the access to data available through the systems interfaces. Additional specification methods, however, are required to state restrictions on the information encoded in this data.
In KASTEL, we use information-flow properties of components. The Method allows to specify which information of incoming data may be encoded in the data leaving a system. The semantic definition of the specifications is formally founded, such that security can be guaranteed, in particular, for compositions of components.
Contact
Referenzen
- Specification and Verification of Confidentiality in Component-Based Systems Poster at the 35th IEEE Symposium on Security and Privacy




